Conversations around QR codes on business cards (not QR codes in delivered packages) and if the QR code on that business card is safe (spoiler alert: yes it is safe)
Narrative:
There is currently conversation on Nextdoor around scams utilizing QR codes, as well as a company placing business cards with a QR code under windshield wipers. At least one Nextdoor user accused the business placing cards on cars of being one of the scammers/hackers. A Nextdoor user posted a photo of the QR code. I decided to use that QR code to run tests to see if the business cards with the QR codes are malicious or not.
Procedure:
I fired up an Android test device that’s isolated from the rest of my network. I used a program called tcpdump on my firewall in order to monitor and record traffic coming to and from that test device. I piped the output from that into a utility called tree so that I could save it and monitor it in real time at the same time. Then piped that back into tcpdump and piped that output into tree again as plaintext and monitored and saved that. I was left with two files: a dump file that could be opened in WireShark, and a txt file that listed all of the output as regular plain text.
This gave me a baseline of activity that my android device was doing before scanning any QR codes. I repeated the steps above while scanning the QR code.
My next step was to take the plain text output of both and pipe the output through filtering utilities like grep and sed to have only IP addresses and not the other information. I piped those through the utilities sort and uniq and so all that was left was a list of IP addresses BEFORE scanning the QR code, and IP addresses AFTER scanning the QR code. Then I piped everything through diff and was left with ONLY ip addresses that were not a part of the baseline (i.e. the IP addresses of servers visitied by scanning the QR code)
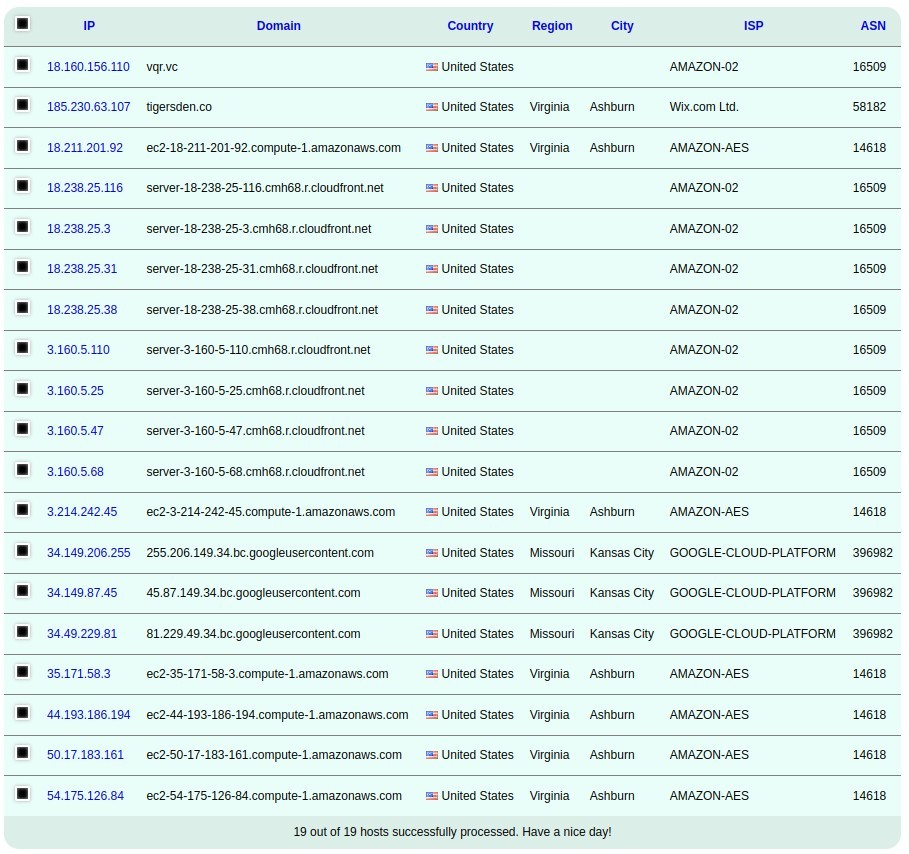
Those IP addresses were run through ip2location.io and infobyip.com for some basic information like location, hosting, and domain names.
Next I ran the domain in the QR code, as well as the domain the first one links to, through dnslytics.com for some more domain information.
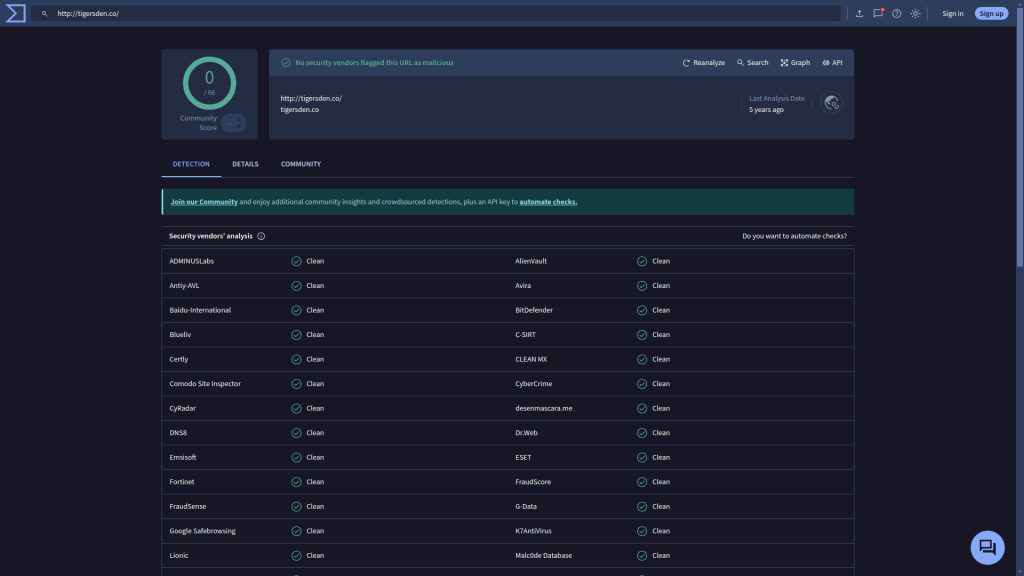
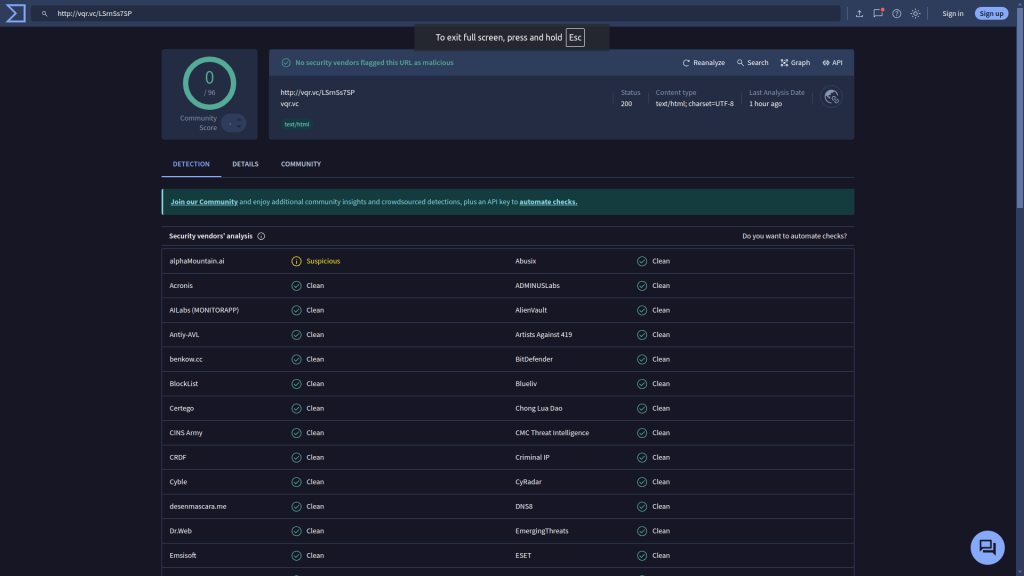
Then, I ran the QR code link, and the destination link through virustotal.com.
Finally I examined the dumps in WireShark after filtering out IP addresses from the baseline checks.
Results:
It is not malicious
The servers contacted are all web hosts.
The first link is to a company that creates QR codes for you to link to, and then shares information such as “How many people scanned my QR code this week?” “Are there more people scanning this with Android or with iOS?” “What cities are the people scanning my QR code in?”
The second link is just the company website.
Neither website was shown to be malicious in virustotal.com‘s URL scanner
list for https://www.infobyip.com/ipbulklookup.php:
vqr.vc
tigersden.co
18.211.201.92
18.238.25.116
18.238.25.3
18.238.25.31
18.238.25.38
3.160.5.110
3.160.5.25
3.160.5.47
3.160.5.68
3.214.242.45
34.149.206.255
34.149.87.45
34.49.229.81
35.171.58.3
44.193.186.194
50.17.183.161
54.175.126.84