Re-posted from a post I made on Nextdoor
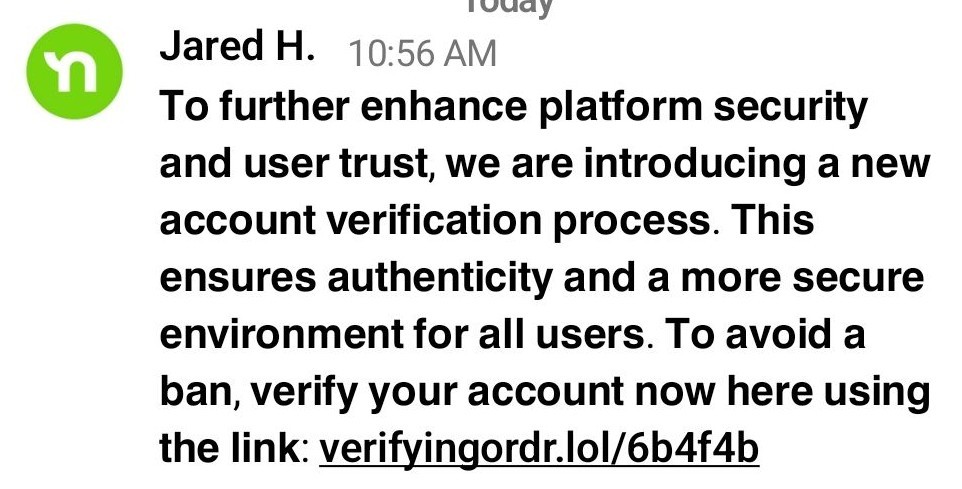
Whoever is in control of the Nextdoor account “Jared H.” in “Mill Hill” is a scammer. I’m not saying Jared H. is a scammer, but whoever has control of that account is.
Thank you to the Nextdoor Neighbors that brought this account to my attention. If you come across suspicious posts or chat messages (especially from that user, please report them to Nextdoor).
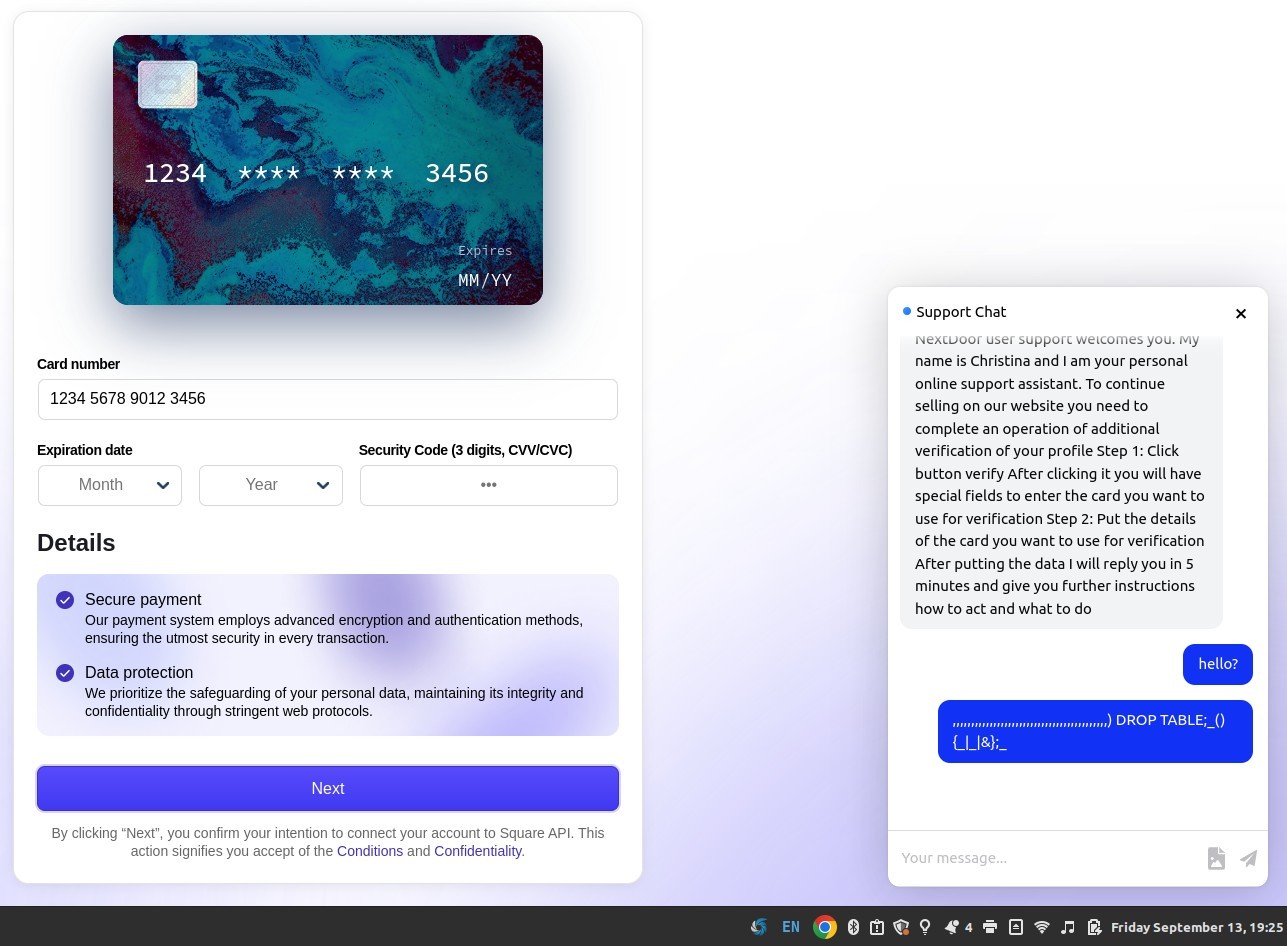
There are some red flags in the message and the link. To me, the most telling part is the fact that these DMs came from a seemingly random user impersonating Nextdoor Support. Nextdoor Support does not reach out to end users in this manner.
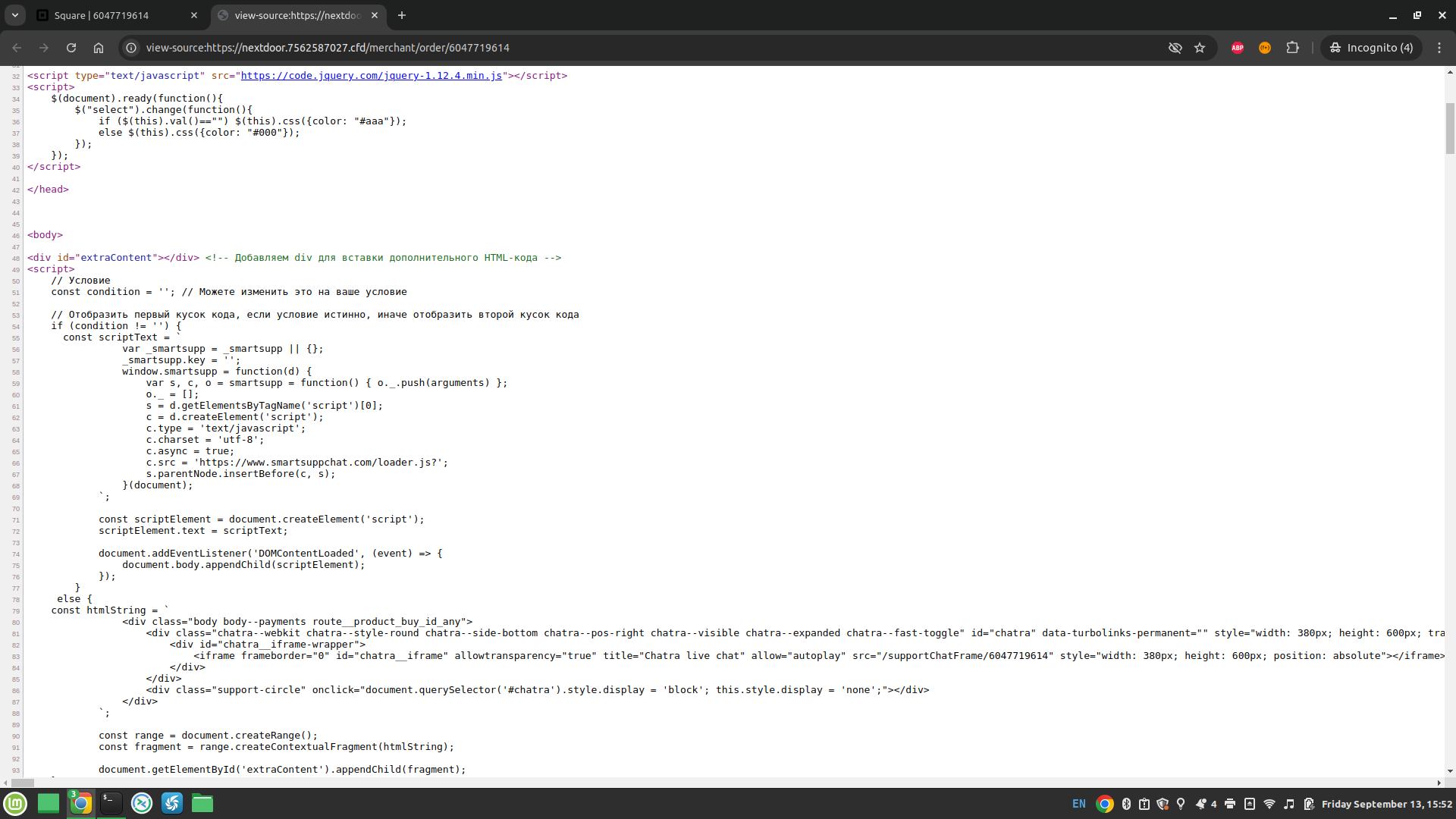
Additionally, the domain of the link in the DM is NOT a Nextdoor website. All the website does is re-route whoever clicks on it to another website. That website, also not a Nextdoor owned website, impersonates Nextdoor and asks for credit card information, ostensibly to verify your identity.
The wesbites were both registered today. As we all know, Nextdoor is older than one-day-old.
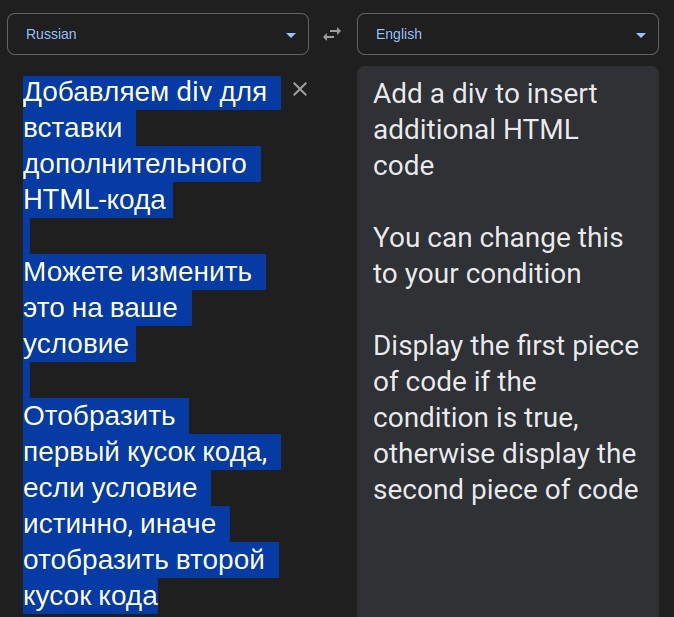
I looked at the source-code, and it contains publicly available code for credit-card stealing webpages, as well as some writing in Cyrillic. I put the Cyrillic into Google Translate, and it was identified as Russian (Nextdoor is not based in Russia, nor programmed in Russian).
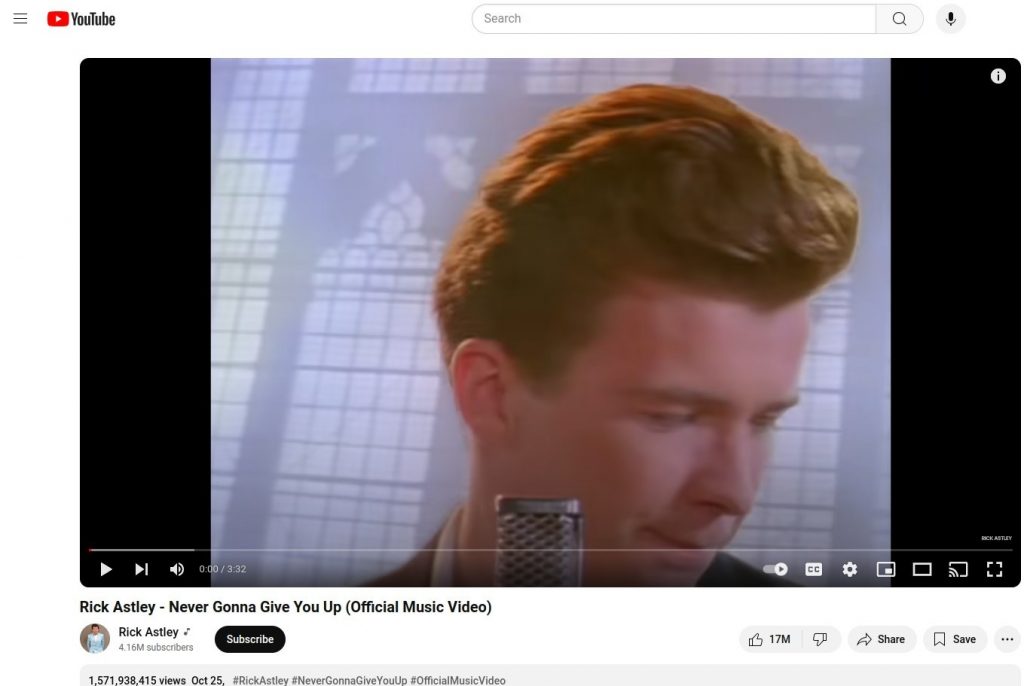
Finally, at the bottom of the source-code, was a link to a Rick Roll (a YouTube video of “Never Gonna Give You Up, which used to be a common prank)
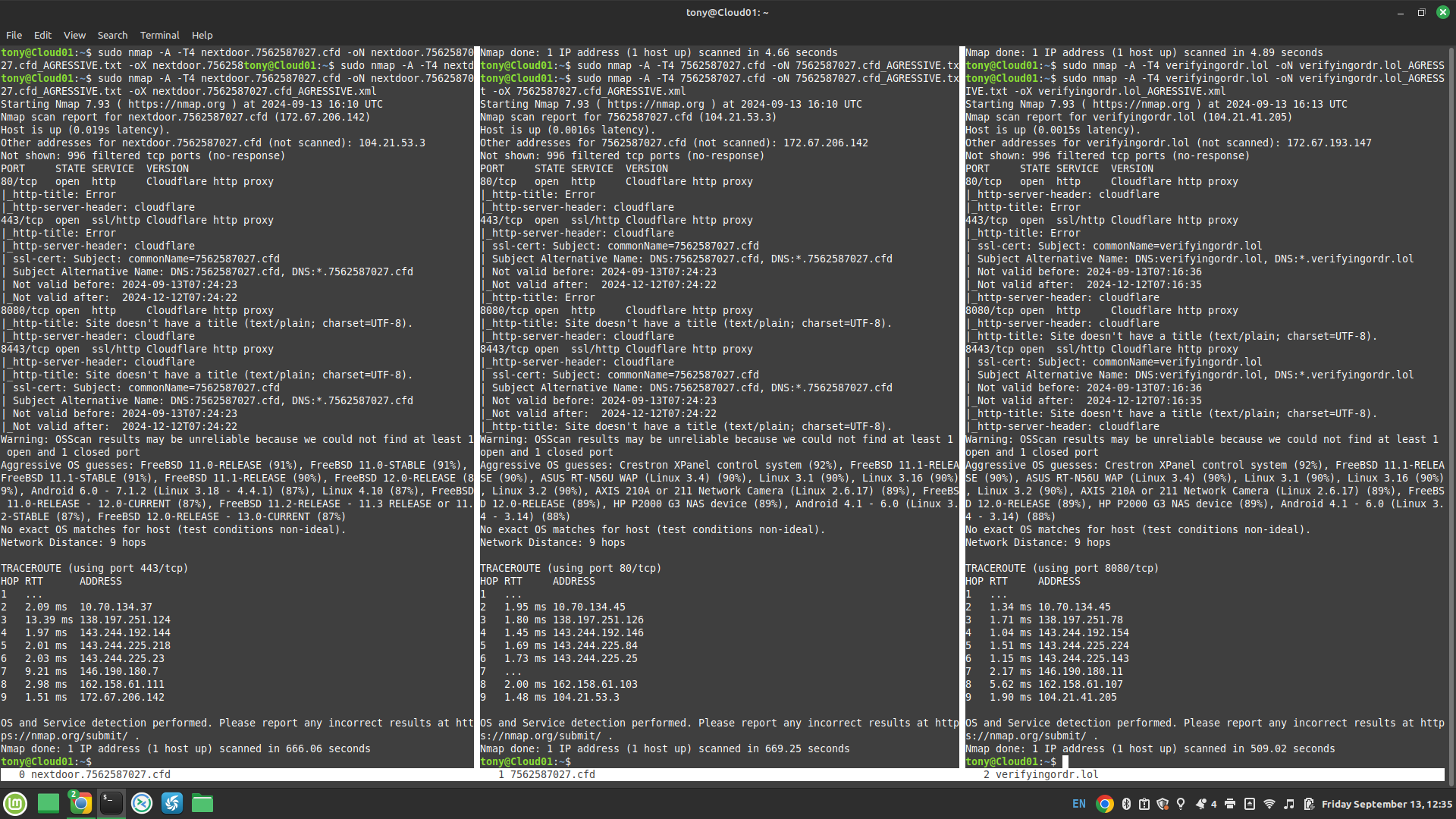
I then looked to the webservers hosting these websites. They each have unique IP adresses, but other than that, they appear identical. Running them through some OsInt tools didn’t yield any useful results either, except that they are now beginning to slowly classify these sites as threats.
Additionally, each link to the first website is unique, which leads to a link to the second website which is also unique, and the reason for this is that the final page is customized with the target’s name to lend credibility. Using a link that goes to another link, or layering, aids in hiding the scammer websites, as well as helping to keep the scamming sites around longer, because the first link, essentially a decoy, will not flag most malware detectors because they’re just a re-direct, so even with anti-virus, the link will appear to be “safe”
Please let me know if you have any questions!
https://verifyingordr.lol/6b4f4b -> https://nextdoor.7562587027.cfd/1770969236 -> Martin Chaney
http://verifyingordr.lol/dc11af -> https://nextdoor.7562587027.cfd/6047719614 -> Kathy Henson